VPNs, when managed properly, are a great way to protect your privacy and keep your online activities hidden from prying eyes. But not all VPN services maintain the same security standards or take the exact same approach to user privacy.
How does your VPN handle your data? When the police or governments come knocking, what does your VPN do? The history of law enforcement subpoenas of VPN logs is murky to say the least. Major VPNs can get hundreds of data requests per year, but what they turn over is not so straightforward. I’ll try to clear the water and help you understand how your data is being handled and how safe it truly is.
VPN warrants and data request handling
VPN providers typically receive two different kinds of data requests, those regarding copyright violations through a DMCA (Digital Millennium Copyright Act) request or requests from law enforcement or government authorities following up on other possible illegal activity.
By far the most common are DMCA requests, which can oftentimes range in the tens of thousands per month. Law enforcement requests are much less common and may range on average from a few per week to one per day for the largest VPN companies.
We can get a more accurate glimpse of these numbers by looking at each VPN provider’s transparency report (more on those later) posted on their website. Our top pick, ExpressVPN, states that in the period from July to December 2023, they received 194 total “Government and/or police requests” and 152,653 DMCA requests. Another extremely popular service, NordVPN, reports 81 total “inquiries from government institutions” from January to April 2024 and an astounding 2,421,053 DMCA requests — clearly NordVPN is the people’s choice for illegally pirating material. For what it’s worth, both companies state that none of these requests resulted in the disclosure of user information.
Other popular services such as Private Internet Access (PIA), CyberGhost, ProtonVPN, and Surfshark also post this data on their websites. PIA received 161 total “government demands for user data ” in the first four months of 2024, while Cyberghost and ProtonVPN received a fraction of these across all of 2023, a total of three and 60 respectively. Surfshark has unfortunately not updated their transparency report since 2021, but as an interesting aside, they used to break down which specific companies and countries had submitted data requests — a third of which came solely from the U.S.
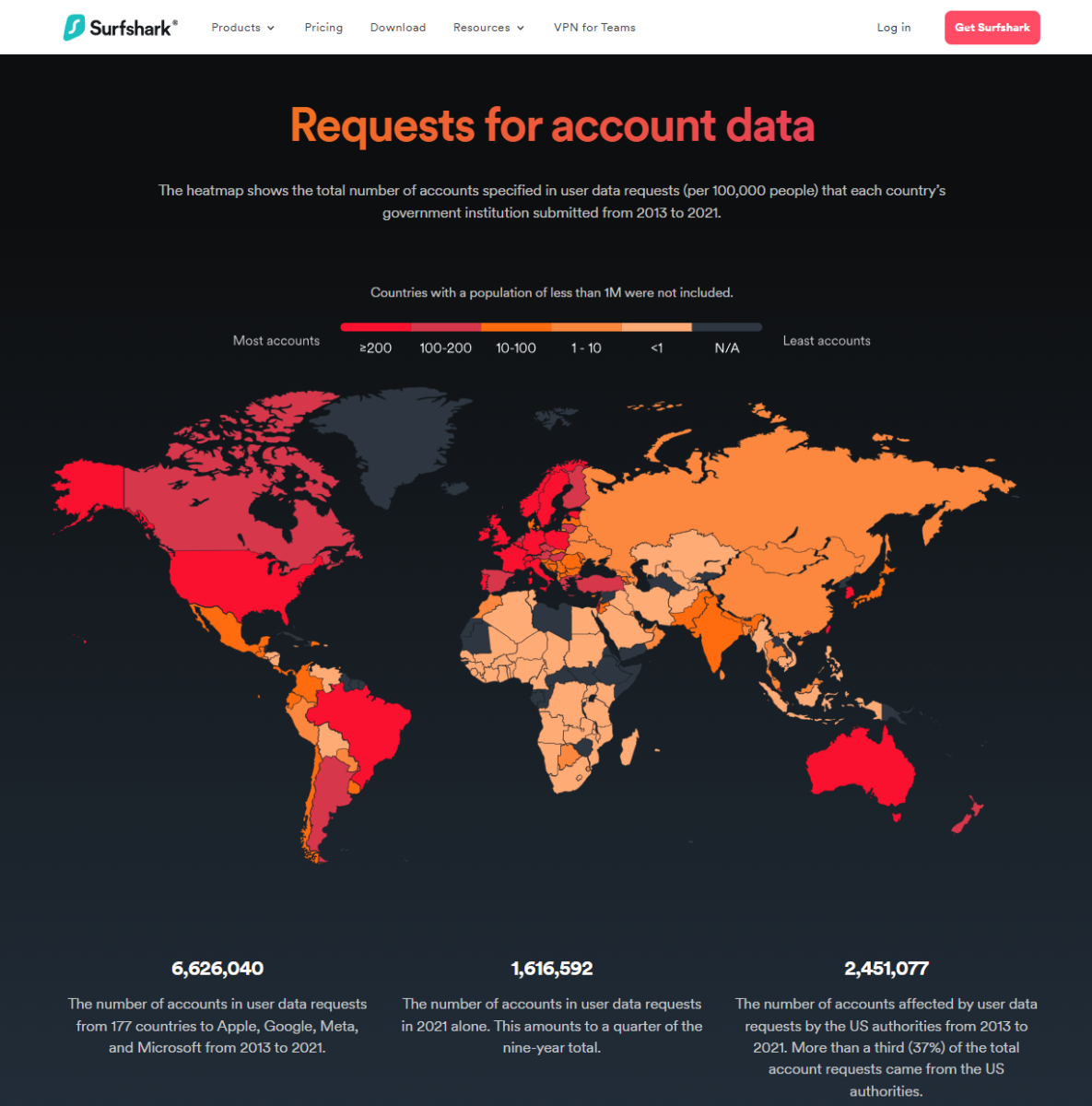
Surfshark’s 2021 annual report shows a heat map of data requests from each country’s government.
Surfshark
Most VPN providers claim to have a no-logs policy. What this means is that they do not collect and store user data transmitted through their network. In a perfect world, no data about where you go online, what you download, or what your search for is recorded. Whether or not a VPN lives up to these standards is an issue that warrants its own separate discussion.
Even with these no-log promises, it doesn’t stop law enforcement or other authorities from attempting to subpoena that data when it thinks an illegal activity has been committed over a VPN’s servers. And when they come calling, there isn’t much a VPN can do to stop them.
In 2016, U.S.-based IPVanish was served with a Department of Homeland Security “summons for records” requesting user data about a suspected felony. After initially claiming they had no information to give, the company subsequently turned over some data on that user to the government.
Other documented instances include a data request in 2016 to PIA and a 2017 request for logs from PureVPN, both by the FBI. PIA remained true to their no-logs word by proving they had nothing to give the authorities, while PureVPN went on to secretly work with the FBI to provide an IP address of a user leading to an arrest.
There are also instances where more extreme measures were taken against VPNs. In 2017, ExpressVPN famously had its servers seized by the Turkish authorities. No data was obtained as a result, further bolstering ExpressVPN’s no-logs claims.
While it’s undoubtedly crucial that authorities receive the help they need to capture dangerous criminals, the extent to which VPNs can assist varies widely.
How do you know if your VPN has received a data request from the authorities
The history of law enforcement warrants, subpoenas, and data requests is intentionally opaque. On the one hand, law enforcement doesn’t want to tip their hand to the very people they may be trying to find. On the other, VPNs have an incentive not to disclose these warrants as they could potentially drive paying users away from the service.
However, in recent years we’ve seen VPNs turn a corner towards more transparency. Placing user trust as their highest priority, major VPN services are becoming more open about data requests.
Gone are the days of hush-hush data seizures. Nowadays, VPNs often employ clever tricks to alert users to requests. Such things as warrant canaries can sidestep gag orders and publishing regular transparency reports detail all data requests over a given time period. These are a welcomed change for many in the user-trust VPN business where privacy is the many selling point.
Warrant canaries
Warrant canaries are intended to alert users to when the VPN service has received a warrant or serious data request from authorities. Typically, a warrant will place a gag order on the company from disclosing the issue or alerting users. Warrant canaries are an attempt to subvert these gag orders.
The way that warrant canaries work is simple. Every few days or so, the VPN service will publish a note stating that the company has not received notices from authorities. If and when a warrant is then received, this will trigger the regular notices to stop updating, indicating to users that something isn’t right and to temporarily proceed in using the VPN with caution.
Transparency reports
A more recent trend for many of the top VPN providers is to switch from warrant canaries to regular transparency reports — usually posted monthly or quarterly. VPN services claim transparency reports can provide details and clarity that are lacking in warrant canaries. The drawback here is that warrant canaries potentially inform users as soon as there is a request from authorities whereas transparency reports will only inform users a month, sometimes many months, after the fact.
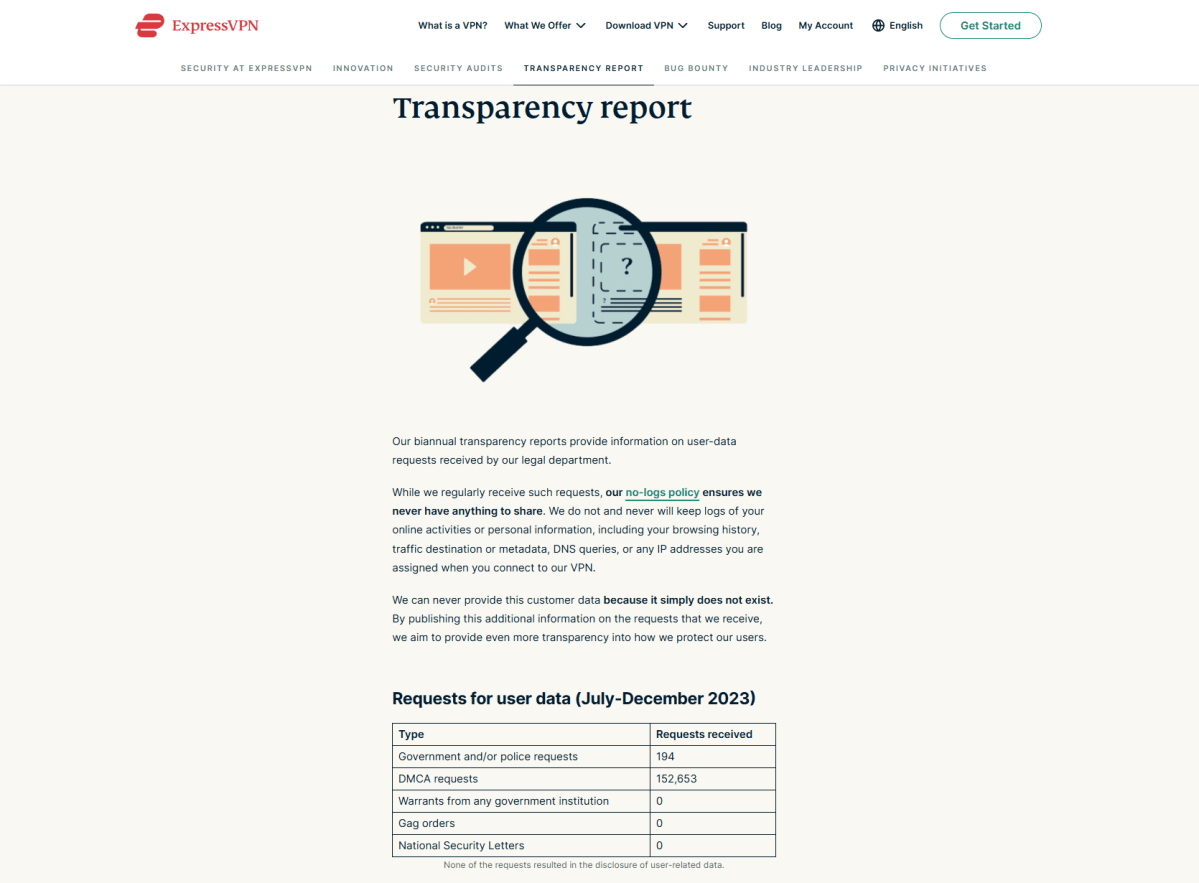
ExpressVPN’s 2024 transparency report lists how many data requests it received, their origins, and if any data was provided.
ExpressVPN
Transparency reports will usually display details such as the total number of government and/or law enforcement requests as well as DMCA requests from production companies and law firms. Oftentimes the VPN will also disclose if any of the requests resulted in the disclosure of user-related data.
How to choose a safer VPN
So what does all of this mean for you? Well, it’s a clear sign that choosing the right VPN for your privacy needs is paramount. You don’t want to choose a VPN thinking you know how they’re handling your private data and then come to find out that behind the scenes they’ve been doing something different the whole time.
The fundamental problem with even the best VPN, is that you can only truly take them at their word. All the independent audits and transparency reports in the world are still not enough to completely verify what the VPN is actually doing with your data from moment to moment. This may not be a huge concern for the average user looking to stream out-of-area Netflix, but for journalists, political dissidents, and other high-risk individuals it could be a matter of life or death.
If your main reason for choosing a VPN is privacy, then you’ll want to look for one with a strict no-logs policy. This means checking the company’s Privacy Policy (usually found on their website) for what data they do and do not collect.
Next you’ll want to check to see if that company has completed any independent security audits. These are audits by third parties of a VPN’s servers to confirm that they have no vulnerabilities and verify their no-logs policy claim. Better yet, look for a VPN provider who goes through regular (bi-yearly or yearly) audits to make sure they’re continuing to follow up on their promises.
You’ll also want to look for a VPN that is headquartered in a privacy-friendly country, out of the reach of international intelligence sharing agreements and data retention laws. The company should own its own servers (rather than renting them from a third-party), and those servers should be RAM-only to ensure your data is never stored beyond server reboots.
Additionally, a little research about a VPN provider’s history will help you better understand their privacy track record. The incident in 2017 with ExpressVPN is a great example. The Turkish authorities came up empty-handed, further bolstering the company’s no-logs reputation. No VPN is perfect, but by taking these safety measures you can feel more confident that your data remains as private as possible.
See PCWorld’s list of the best VPN services for our recommendations.







