The internet offers a rich selection of tools for criminal purposes: password crackers and vulnerability scanners are just two examples. At the same time, one also finds web applications that are suitable for violating privacy — for example, reverse searches for the owners of telephone numbers or a person in a photo.
However, these tools can not only be used for criminal purposes or to find out the identity of other people, you can also use them for your own protection or for emergencies. Password crackers, for example, are often the last resort if you have forgotten an important password. Vulnerability scanners can also be used on your own network to detect and then block possible entry points for hackers.
Caution: Cracking passwords or even spying on networks is only permitted by law if it involves your own passwords and your own network. If you try to decrypt someone else’s password or spy on another network, you are liable to prosecution.
Replace Windows password
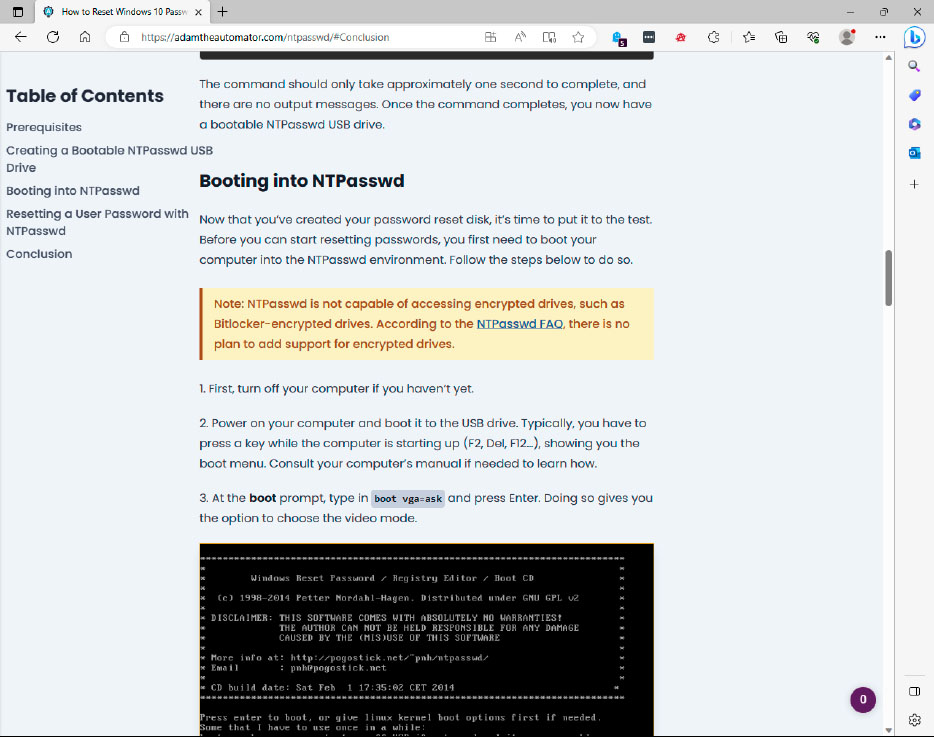
The Offline NT Password & Registry Editor can also overwrite Windows 10 and 11 passwords. A detailed guide on the web explains how to do this.
IDG
The first password you have to enter after turning on your computer is usually the Windows password. If you no longer know this password, your data is not lost — you can boot the computer with a boot stick or a boot CD, for example, and copy important documents to another medium — but you usually have no choice but to reinstall the operating system.
The free tool Offline NT Password & Registry Editor offers a way out. It does not even try to crack the password, but simply overwrites it with a character combination of your choice.
The tool is already quite old, the last version dates from 2014, but it still runs under Windows 10 and 11, albeit with some restrictions. For example, the computer must support legacy mode when booting; the program does not work with a UEFI boot. In addition, the hard disk or SSD must not be encrypted with Bitlocker or any other software.
Also note that Windows’ built-in encryption, the EFS file system, is tied to the password. If you change it with the Offline NT Password & Registry Editor and had previously encrypted your hard drive, the data will be lost.
A guide on how to use the Offline NT Password & Registry Editor can be found here.
Passwords of Office documents
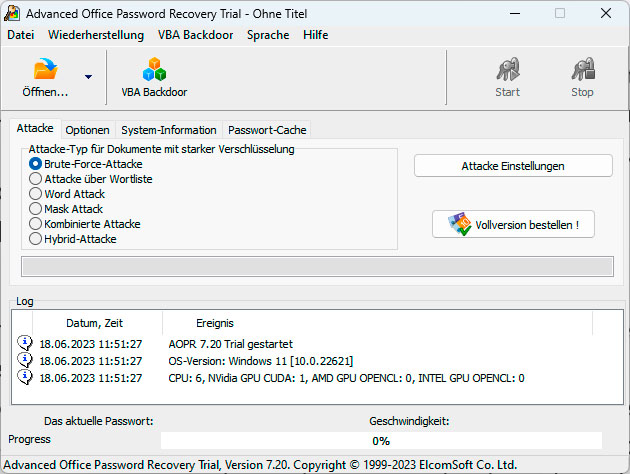
The tool Advanced Office Password Recovery from Elcomsoft knows several methods to crack the password of a locked Office file. In the free version, it finds passwords with a maximum of three letters.
IDG
Microsoft 365 programs such as Word, Excel, PowerPoint, etc. can password protect and encrypt documents. Microsoft has strengthened this encryption somewhat with each new version.
You can therefore find a whole range of tools on the internet that can crack the passwords of older Office versions, but this is hardly possible with the newer builds of Microsoft 365.
One exception is Elcomsoft Advanced Office Password Recovery, which can decrypt documents from all Microsoft Office versions. According to the manufacturer, the software can also determine the passwords of Wordperfect Office, Openoffice.org, and several other Office packages.
To ensure that the process does not take too long, the software uses one or more GPUs. The tool is available for a fee, the home version costs $49. The manufacturer offers a test version for free download, which, however, only displays passwords with a length of up to three characters, which will hardly be sufficient in any case.
PDF documents that you have password-protected via Adobe Acrobat or Word are a special case. For them, you need a separate program, namely Elcomsoft Advanced PDF Password Recovery for $49 as well. A limited test version is also available for this tool.
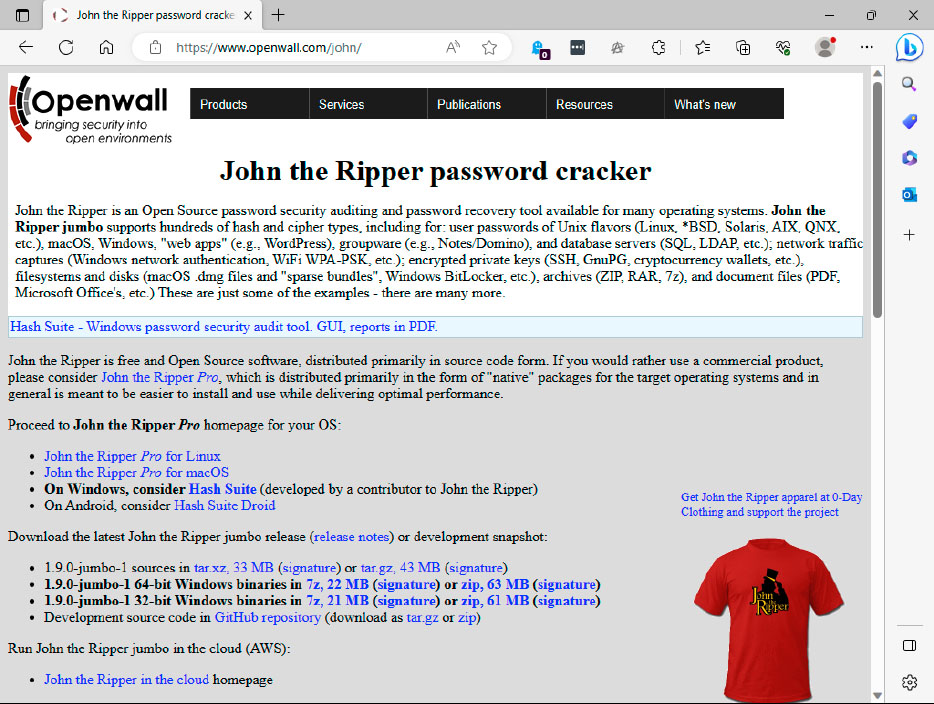
John the Ripper is an open-source program that cracks passwords from various Office formats and other programs thanks to several extensions. However, this can take several hours or even days.
IDG
The alternative to Elcomsoft is the free command-line program John the Ripper. You control the software via the command line, so the operation is a little more complicated. With the help of extensions, however, you can use the tool for decrypting Microsoft 365 files as well as for Libre Office or encrypted ZIP files.
Try out how long the Elcomsoft programs and John the Ripper take to determine a password you have used. This will give you an idea of how secure your password really is. Keep in mind that criminal hackers may have access to current high-performance computers with several GPUs and correspondingly high computing power. Their performance can exceed that of a PC by a factor of a hundred or more, at least when it comes to such special tasks.
Scan your own network
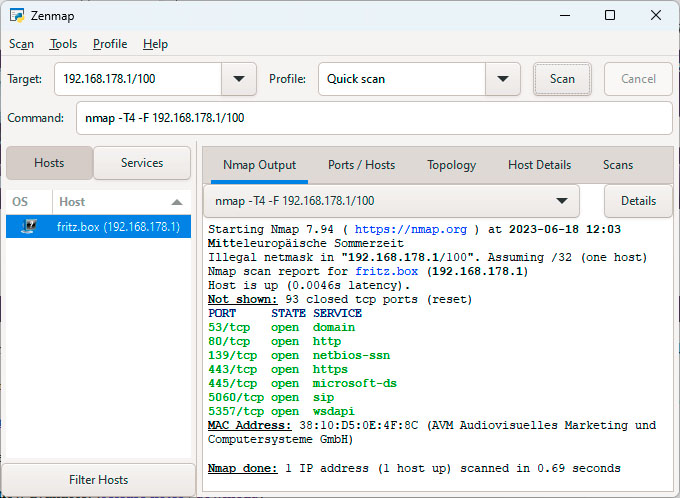
Nmap was originally a Linux tool for the command line. In the meantime, a Windows version with a graphical user interface is also available, which makes it much easier to use.
IDG
If malware manages to get onto your computer, it will often try to infect other computers in your network as well. As a preventive measure, you can subject the devices in your network to a vulnerability analysis. The best-known tool for this is the open-source software Nmap.
It looks for open ports through which the device could be accessed from the outside and infers the operating system, its version, the running services, and the installed firewall from the port configuration and other data. If vulnerabilities are known for a found configuration, a criminal hacker can exploit them and take over the computer.
Nmap is a professional tool and requires some knowledge about how networks work. At https://nmap.org/docs.html you can find detailed instructions for the program, both for the command line version and for the version with the Windows interface. Research may be required to interpret the data provided by Nmap.
Testing the Wi-Fi password
The graphical user interface of Aircrack-ng is very sparse. Nevertheless, the program is tricky to use and also requires special hardware components to be able to pull data at all.
IDG
The security of a Wi-Fi network depends largely on the password used. For this reason, Wi-Fi passwords are often very long and complex. To crack Wi-Fi encryption, it is also necessary to record and analyze the data traffic between the access point and a client for a long time. Alternatively, carry out a brute force attack and try character combinations until you come up with the password for the network access.
The tool Aircrack-ng goes another way: It searches for the pre-shared key, a key that is exchanged between the access point and the client computer for the encryption of the data. Possible locations are the recorded data traffic in the form of a file or a monitored Wi-Fi network.
Aircrack-ng only works with a number of selected Wi-Fi chipsets and antennas. It is also not easy to operate. In addition, it can realistically only decrypt shorter passwords. Decrypting the 20-digit password of a Fritzbox, for example, is hopeless.
For a security test, however, this feature is just right: If Aircrack-ng can crack your Wi-Fi password, it is too short.
Hiding your identity on the internet
The Tor network is still the best choice for moving around the internet undetected. It is true that registration via Tor is also a prerequisite for visiting the Dark Web, where illegal goods are traded on many sites.
But Tor is also the safest way for many people in repressive states to access websites undetected that are not accessible in their own country. Here in the United States, TOR is simply a secure way to remain anonymous on the internet. You can also send emails or use social media via the network — Facebook has been operating its own site on the Dark Web for several years.
To access Tor, all you need is the free Tor browser, a customized and pre-configured version of Firefox.
If you want to be on the safe side, use a live CD with the Linux distribution Tails, which also allows access to the Tor network, and boot your PC with it.
Reverse search: photos
Pimeyes is a search engine specifically for faces. You can upload a portrait to the website or snap a photo with your smartphone, and the web service will search its database for more pictures of the same person in a split second. It then presents you with the photos it has found and names the websites where it found them.
Three searches are free, but the service does not name the corresponding web addresses. You have to pay $14.99 per search to activate them. For further searches, you take out a subscription, which costs $29.99 per month in the cheapest version.
Google also offers a similar service free of charge. The search engine offers an image search at www.google.com/imghp. If you click on the camera symbol to the right of the search field, you can upload a photo. After clicking on “Search,” adjust the image section and then click on “Search image source.” Google will then present you with a list of which websites this photo appears on.
There is one difference between the two services: Pimeyes is able to search for pictures of the same person, so you can identify them by a caption, for example. So it is a service for face recognition. Google’s image search, on the other hand, only finds the same or similar photos on the web. However, both search engines can be used usefully to search for unauthorized use of copyrighted images, for example.
This article was translated from German to English and originally appeared on pcwelt.de.


